AMP for Endpoints features can be summarized in:
- Endpoint malware prevention/detection.
- Malware tracking across all deployed devices.
- Proactive prevention by detecting vulnerabilities and suspicious file monitoring.
AMP for EP provides two types of protection:
- Cloud based protection (See AMP 101):
- Check the hash of the file against the AMP cloud and this tells us if the file is good or bad (worth mentioning it checks the hash against Virustotal as well).
- If the file turns out to be unknown, we will send it to the cloud for sandboxing.
- Offline protection:
- ClamAV engine for offline scanning.
- TETRA engine. (Bitdefender engine) which allows us to perform offline scanning, rootkit scanning, and other things that a traditional antivirus product does. Its major draw back is compatibility with other antivirus products and should never be enabled if another antivirus product is installed on the computer.
At this point you might have a question regarding this product. And you are not alone.
Can it be used as an antivirus substitute?
What the vendor might tell you is that they recommend to use a free antivirus (AVG, Microsoft Defender…) for all the signature based protection AND on top of that to use AMP for EP.
However my opinion is, with signature-based systems being more obsolete each day and with AMP for EP already including two offline engines (and who spends time offline anyway?), AMP for EP should be enough.
How do I manage this?
AMP for EP is deployed in the form of a very lightweight client that can be installed in Windows, Mac OS, Linux… and that synchronizes to your AMP Cloud account.
Then from a web dashboard you manage and monitor your endpoints. Easy as that.

AMP for EP is surprisingly easy to deploy and manage. Even more surprising after seeing the Cisco logo.
Let’s go into details.
One of the more cool features for me is the interface as it’s very interactive and intuitive. An example is that everytime we see a hash on a menu, we can R-click on it and dig into details.
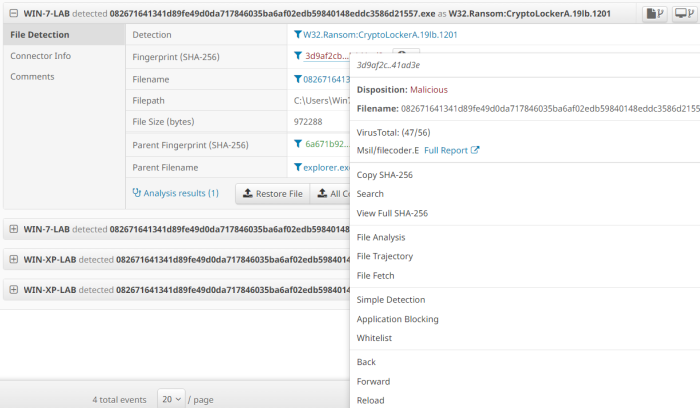
R-click and you get access to see how many AV do detect this file as malicious in Virustotal (47/56 and this was an old version of Cryptolocker 2…shame!).
From this menu we can also access a few interesting bits:
File trajectory:
This feature will allow us to track in which devices has a file been detected, but doesn’t appear to work if the file gets quarantined.
File analysis:
After submitting a file to the sandbox (Threatgrid) this will provide us with a threat score and a report for the basic and dynamic analysis of the file. It includes a detailed explanation for every behavioral indicator seen, really useful for those who haven’t devoted their life to malware research.
Also we can play a video of the VM running the program (did I mention that you can choose the OS?), download a .pcap file of the traffic generated by it, and download all files that have been created during the running of the file.
Overall a really detailed report, as you would want it to be.
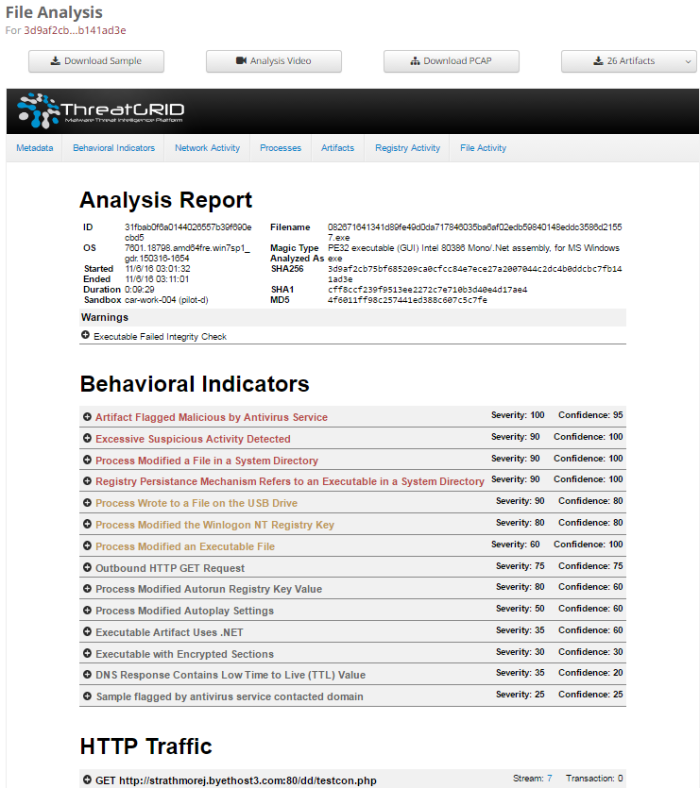
Deconstructing Cryptolocker.
Vulnerable Software
In this page AMP will report those devices running software that is on a version with known vulnerabilities.Plus it will tell us which CVE apply to that version, the severity of it, and will provide a link
At the time of writing the following applications where checked for vulnerabilities:
- Adobe Acrobat 11 and higher
- Adobe Acrobat Reader 9 and higher
- Aobe Flash Player 11 and higher
- Google Chrome 25 and higher
- Microsoft Internet Explorer 8 and higher
- Microsoft Office 2007 and higher
- Mozilla Firefox 10 and higher
- Oracle Java Platform SE 1.7.0 and higher
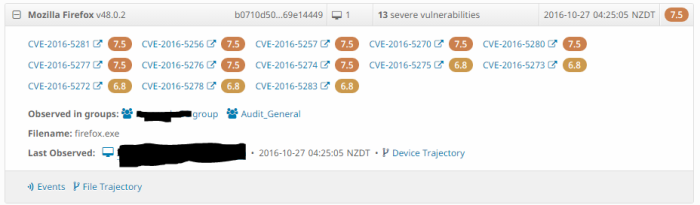
Yes I use Chrome.
Device Trajectory:
AMP tracks all file events and will log all processes/events related to an infection. With a storage of approximately 9 million events this gives us a lot of insight of anything that happened in the last days.
We will be able to track all the processes that lead to an infection with plenty of detail
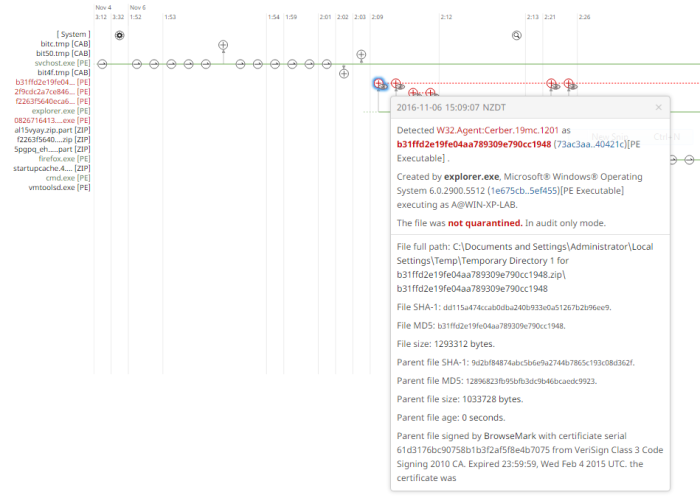
Everything you might need for your post-infection investigation will definitely be here.
There are a couple of more features such as prevalence that are also interesting, if you want more details the FireAMP user guide will be useful.