On the top black menu we will find the main menus of Firepower:
Overview & Analysis:
To view the data.
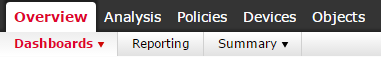
Overview will provide graphs and general statistics through Dashboards. Analysis provides an interactive way of viewing the data trough the Context Explorer and also a more detailed information on
Policies
To decide how to treat the data.
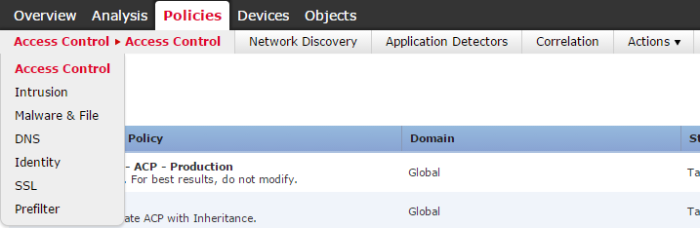
How we deal with packets will be configured through multiple policies. This modular approach allows for easy manageability in bigger projects.
A briefing of these policies:
- Access Control: Basically the brain of Firepower. The AC groups all other policies and sets the flow of packets through them. It is configured through a set of rules on actions to take for the matching traffic.2.
- Intrusion Policy: Configures the Snort engine that drives the IPS. Here we configure/tweak which connections do we want to flag as malicious.3
- Malware&File: Controls what we do with files that move through our network. Do we want to block/allow/log/sandbox them?4.
- DNS: (new!) To allow/block traffic depending on the domain name requested for the connection based on whitelist/blacklists. Looks like Cisco is already integrating OpenDNS in some way here.5
- Identity: Integrating traffic on the network with LDAP or AD.
- SSL: Managing what we do with encrypted traffic (decrypt it even!).
- Prefilter (new in 6.2): This is the substitute of ye old Access Control Lists (ACL’s)
Devices:
There are few things we can do here:
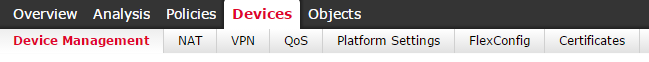
- Add/remove and monitor the status of the ASAs we want to manage from the FMC.
- Configure most Layer 2/Layer 3 parameters from the ASAs. Enabling interfaces, IP addresses, DHCP Servers, NAT…
- VPN stuff.
Objects:
To define objects we can use through our configurations (Networks, devices, ports…) and play with Snort rules.
AMP:
To configure parameters related to connecting our ASA to the AMP cloud or in case we want to synchronize information between an AMP for endpoints deployment and our ASA.
Deploy
To push the configuration changes to the appliances. Includes an option to verify the consistency of those configs, similar to Checkpoint.
System:
System configuration: User credentials, configuration of multitenancy, licensing…
Help:
F1.
