Following the Firepower Configuration example there are a few steps we can follow to fine tune our appliance:
- Snort rule recommendations
- Whitelisting false positives
- Make it IPS
- Run a nmap scan of your network
Snort rule recommendations
After a few days of gathering data of our network go Policies>Access Control>Intrusion and edit the policy in use.
Click on Recommendations and here set the desired recommendation threshold and if you want snort to disable rules.
For a maximum detection I would suggest:
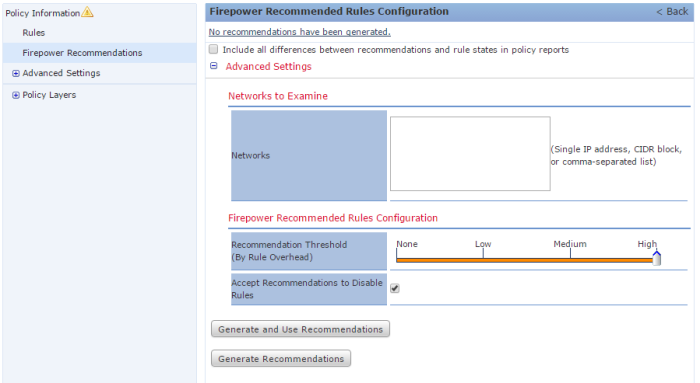
After this you can review them and then applying by clicking on Use Recommendations.
I would recommend you to have a look at the rules. In my case I found that the rules related to Hola VPN were disabled.
While Hola VPN is a free and simple way of bypassing country blocks I would recommend using an alternative, check this article.
So first of all I click on rules and then filter by “hola”, select all of them and choose the Rule State from Disabled to Drop and Generate:
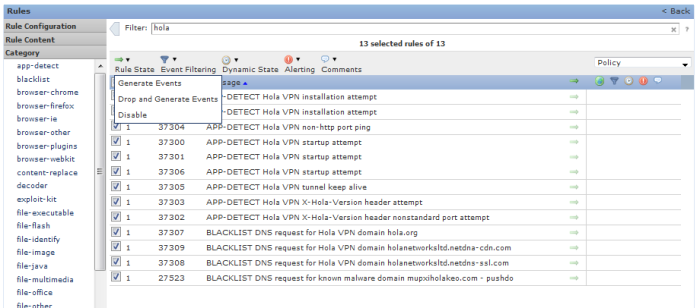
After this click on Policy Information and Commit Changes. Then re-deploy your Access Control policy so these have effect on traffic inspection.
Whitelisting false positives
Make it IPS
Easy. Go to the Intrusion Policy settings and mark the Drop when Inline tick box.
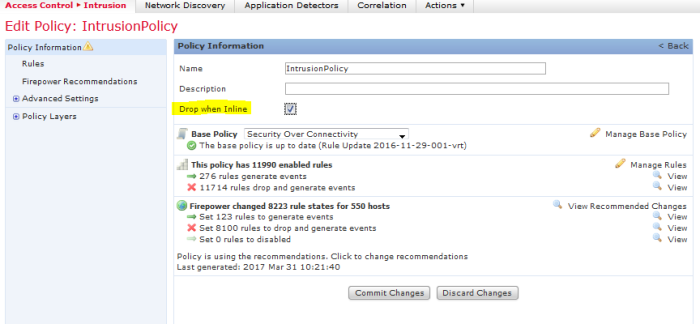
Goes without saying the device has to be in a non-passive deployment 🙂